[Overview]
Oracle WebLogic Server is an enterprise multi-tiered Java application service, commonly used as a large enterprise web application platform.
[Vulnerability Details]
This vulnerability is exploited due to insufficient validation of serialized XML data by WorkContextXmlInputAdapter. An unauthenticated attacker could exploit this vulnerability by sending carefully crafted HTTP XML requests. Exploiting this vulnerability could result in an attacker executing arbitrary code in a user-run WebLogic environment or even directly controlling Ocacle WebLogic Server for mining activity.
Vulnerability Source: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-10271
[Severity]
High-risk
[Impact]
- Oracle WebLogic Server 10.3.6.0.0
- Oracle WebLogic Server 12.1.3.0.0
- Oracle WebLogic Server 12.2.1.1.0
- Oracle WebLogic Server 12.2.1.2.0
[Fix Suggestions]
Upgrade Oracle official patch
Patch download address: http://www.oracle.com/technetwork/security-advisory/cpuoct2017-3236626.html
[Hillstone Networks Solution]
Hillstone Networks has added signatures to the signature database: Signature Library Version: 2.1.222. By deploying any Hillstone Networks solutions with IPS function, XmlAdapter deserialization vulnerability can be quickly detected and effectively blocked to prevent exploitation by the mining program.
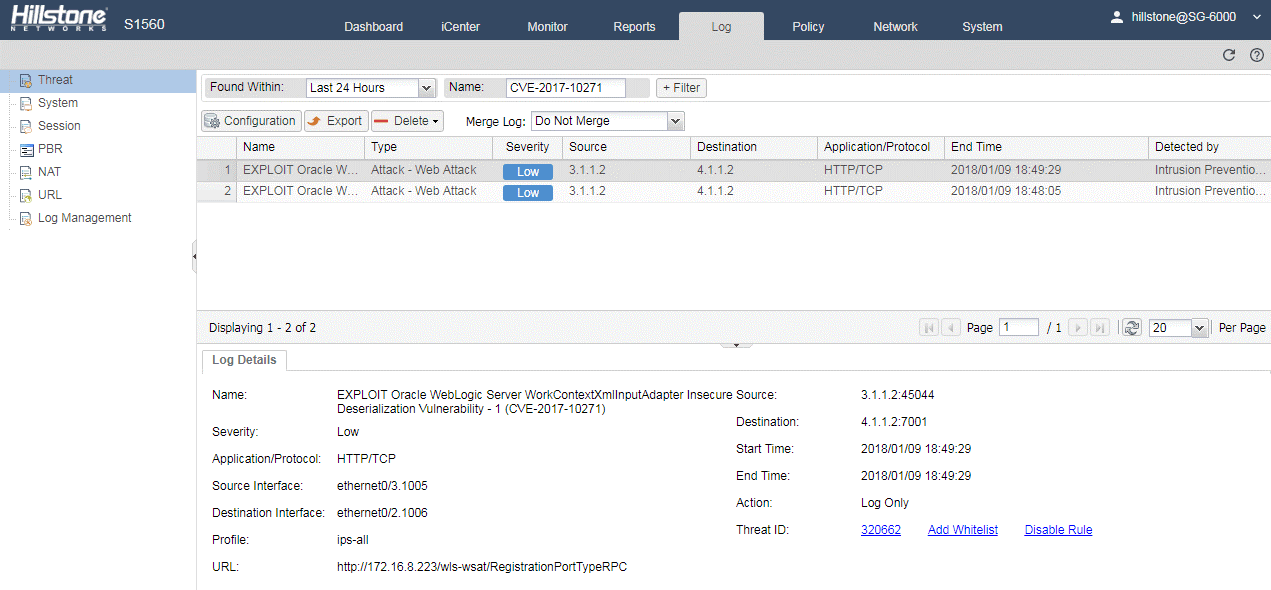
Threat Events Detected by Hillstone Solutions
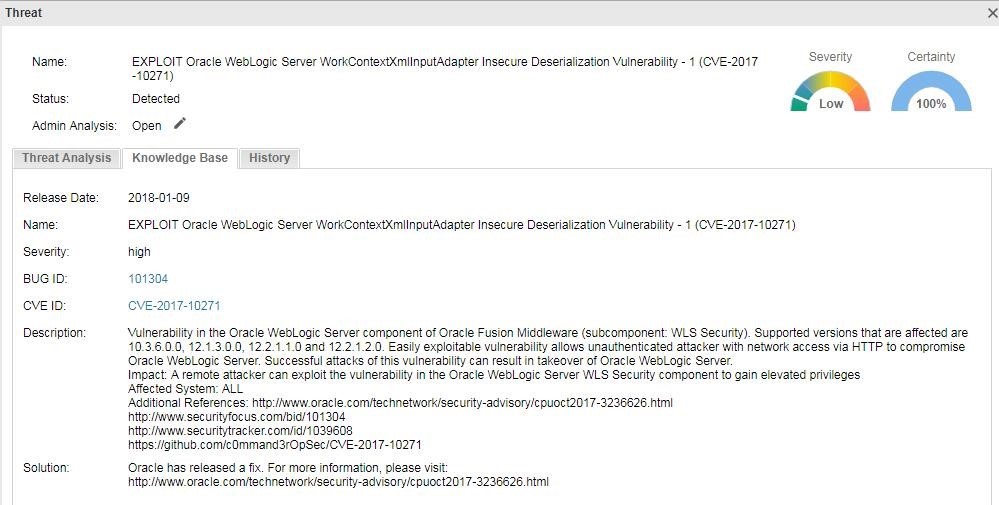
Threat Details