[Overview]
Adobe ColdFusion is a dynamic web server, a rapid application development platform offered by Adobe Systems that contains advanced features for enterprise integration and internet application development.
[Vulnerability Details]
CVE-2017-11284: This vulnerability is caused by no input validation before the object in the RMI registry is deserialized. An unidentified attacker could exploit this vulnerability by sending maliciously crafted deserialized data to the target application. If this vulnerability is exploited, arbitrary code will be executed remotely on the system with the unwitting victim application’s permission.
Vulnerability Source: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-11284
[Severity]
High-risk
[Impact]
- Adobe ColdFusion(2016 release)update 4 and earlier
- Adobe ColdFusion 11 update 12 and earlier
[Fix Suggestions]
- Turn off port 1099 to prevent ColdFusion from communicating with untrusted networks
- Upgrade to the latest version or an officially provided fix to prevent attacks
Official statement: https://helpx.adobe.com/security/products/coldfusion/apsb17-30.html
[Hillstone Networks Solution]
Hillstone Networks has added signatures to the signature database: Signature Library Version: 2.1.224. By deploying any Hillstone Networks solution with IPS function, Adobe ColdFusion deserialization vulnerability can be quickly detected and effectively blocked to prevent hackers from exploiting it.
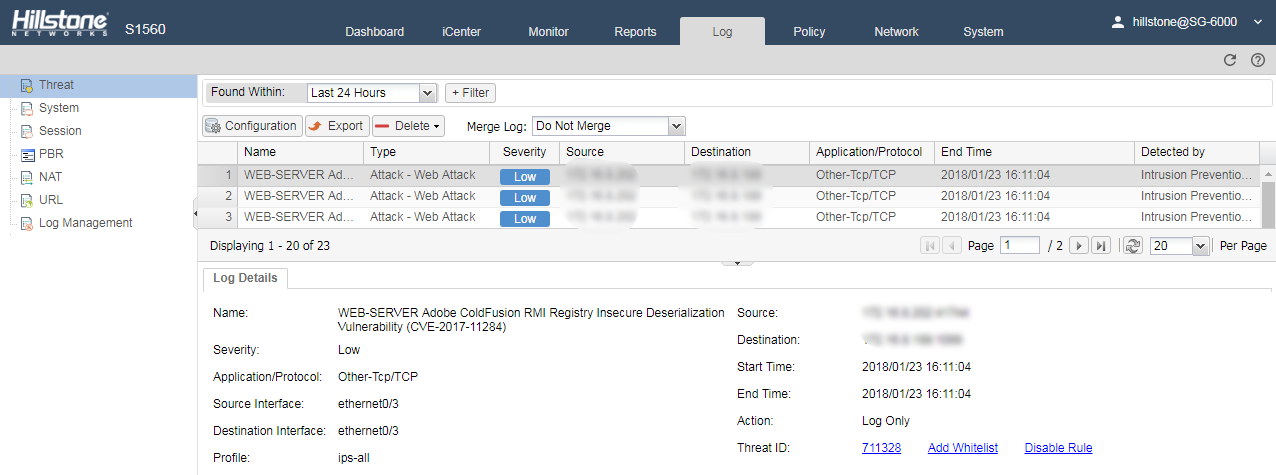
Threat Events Detected by Hillstone Solutions
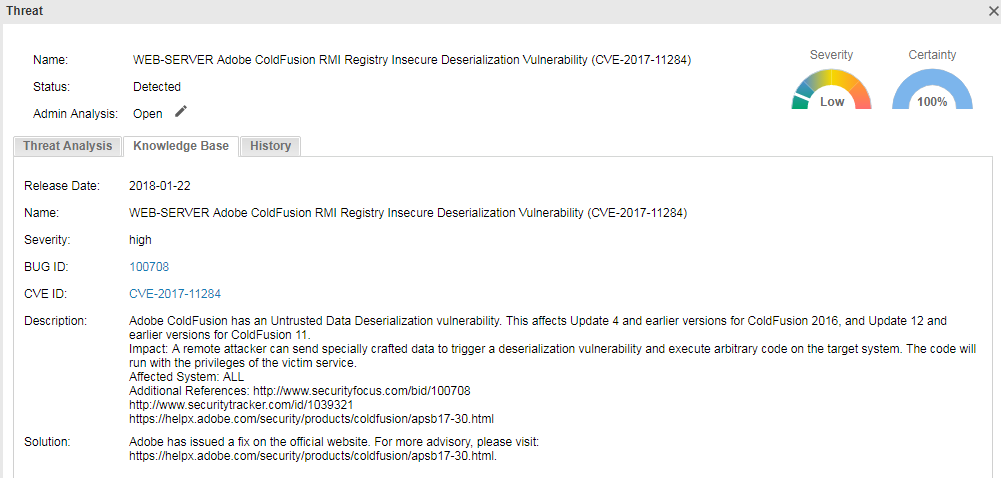
Vulnerability Detail Description